66 Important Jihadist Twitter Accounts (part 2)
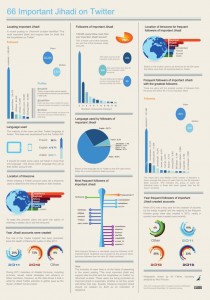
In our earlier post, together with Ali Fisher we detailed and assessed 66 accounts listed by Shumukh al-Islam jihadi Forum member Ahmad ‘Abdallah as ‘important jihadist’ members on twitter. We looked primarily at the users individually, using the data of these 66 accounts to create this infographic to give our readers an overview of these users.
In this post we focus on what we are able to find out about them as a group and provide an interactive network map to show the links between these advocated ‘important jihadist’ twitter accounts.
Relational dynamics
Analysing the relational dynamics between these accounts as a group and those who choose to follow them is a key part of understanding the online strategies of “The most important jihadi and support sites for jihad and the mujahideen on Twitter”.
As we identified previously, the accounts had been categorized in different types by Ahmad ‘Abdallah. This underlines the diverse range of information, which was recommended to further the jihadist endeavour in general. In addition to understanding the specific accounts, the data can be used to analyse the network of individuals who follow the 66 ‘important jihadist’ accounts. The relationships are important as they influence the way individuals search for information, what they find and the behaviours they adopt.
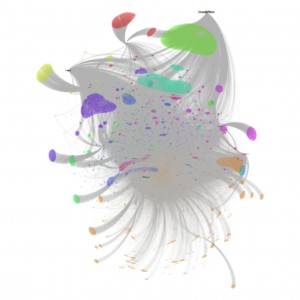
We began by identifying the followers of the 66 ‘important jihadist’ accounts. If each of these accounts were followed by a different group of Twitter users, then this would mean that collectively they were reaching 1.8 million users. However, @mujtahidd alone is followed by over 1.1 million followers, and the real number following the remaining important jihadi accounts is much lower than 700,000. This is because some users follow more than one of the ‘important jihadist’ accounts. Using network analysis, we found that the network following one or more of these accounts (excluding @mujtahidd) was 377235 users and 852948 follower/following relationships. The image below represents the network of important accounts and their respective followers. Each Twitter account is represented by a dot, and those with a follower / following relationship are connected by a line.
The graph (above) shows the network of users identified to be following at least one of the ‘important jihadist’ accounts (excluding @mujtahidd). The colours have been used to highlight the groups of users who follow the same users (or same combination of the 66 ‘important jihadist’ accounts). A quick view of the network image reinforces the previous observation that most of the users are following only one or two of these high-profile accounts in the jihadist online media mind-set. The importance of this combined approach is the ability to analyse the combinations of accounts which users have chosen to follow.
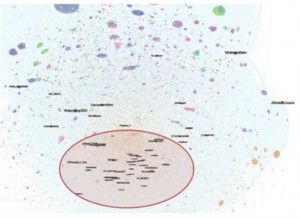
For example, this view of the network shows the concentration of user names near the bottom of the image, (highlighted in red) indicating that there are a number of accounts with fewer followers where the overlaps in follower groups are more pronounced. The Jabhat al-Nusra twitter account (discussed in greater detail here) also has a number of followers in common with the cluster of users highlighted.
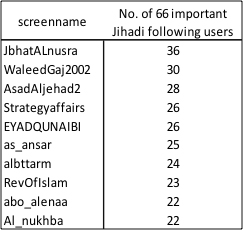
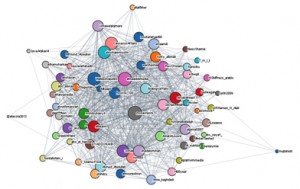
Focusing on the Network of the 66 ‘important jihadist’ Accounts
In addition to the potential to look at the followers of the 66 accounts claimed to be ‘most important’ by the Shumukh al-Islam posting, their profiles and time zones, the relationships between these specific 66 accounts can also provide analysts with insights. For example, JbhatALnusra, WaleedGaj2002, AsadAljehad2 are most frequently followed by the 66 ‘important jihadist’ accounts. Conversely, SaveArakan4, Mhaajrr, housse_100, and alassra2012 appear on the list of the 66, but few other ‘important jihadist’ accounts follow them. The ranking (shown below) is based on frequency of being followed by the 66 ‘important’ accounts are also reflected in the eigenvector calculations for the network. The relationships between the 66 accounts are shown in the image below, and be explored in greater detail by clicking on the image, which will open the interactive version. When using the interactive image, clicking on a node will focus on the connections of that user, double click to open the twitter account of that user.
Please note that the interactive image works best in the Chrome Browser.
The network as a whole represents 958 relationships between the 66 ‘important jihadist’ users with a network diameter of 5 (the distance between the furthest two nodes calculated on the directed graph). The network density is 0.2 on the directed graph (1 would represent a complete graph, where all connections would exist).
Key nodes in the network
In our previous post, we emphasized “we are analyzing these accounts that are defined in this [Shumukh al-Islam] posting as most important for jihadi sympathizers, but it does not necessarily mean that the individual Twitter accounts are an integral part of this worldview.” In this follow-up work, however, we, perhaps not surprisingly, found that the majority of the connected accounts are hard core jihadi media activists. From the above listed, we shall have a look at some of the high-profile hard core jihadist Twitter accounts.
As we analysed JbhatALnusra previously (here, here), let’s have a look at
@WaleedGaj2002
The account has over 45,000 followers while only following 387. Apparently this is the account of “former Guantanamo detainee and eyewitness of the Qila-e-Jangji massacre in Afghanistan” Walid [Muhammad] al-Hajj, from Sudan. According to his latest tweets, he still seems to be on the same page as the mainstream al-Qa’ida jihadis are, appraising Bin Laden and being cherished by other Twitter members for having known the shaykh personally. For further details, here is an interview with al-Jazeera. He was released in 2008. His leaked file is available via The New York Times.
@Strategyaffairs
This is a prolific and quite industrious jihadi media activists with over 100,000 followers and just over a little of 4,000 tweets. He is also active in most classical jihadist forums as ‘Abdallah bin Muhammad. Occasionally he has tweeted statements by the Yemeni AQAP prior to the ‘official’ broadcast within the forums and contextualized as well as posted the statements both within the forums and Twitter. Other Shumukh al-Islam members, for instance, used his Twitter-input to further the AQAP statements within the forum raising @Strategyaffairs status in general (example).
@EYADQUNAIBI
Doctor Iyad Qunaybi is somewhat of a rising star within the radical on- and offline scene. He is active on all social media outlets and his videotaped speeches are also transcribed and published within the jihadist forums. He rose to fame within this subculture in the past year and a half during the troubled times in Egypt and also responded to the jihadi affairs of life in general. By being included on Abu Muhammad al-Maqdisi’s database tawhed.ws, his standing was boosted. Few of his writings and audiobits are available on his author page on tawhed.ws under Iyad al-Qunaybi. His input is valued, re-tweeted and re-disseminated within the forums, on Facebook, and further published on sites such as justpaste.it, see here for example.
@as_ansar
This is the official Twitter account of the bi-lingual Shabakat al-Ansar al-Mujahideen. The main forum is in Arabic and down and out for some time now. The English forum works. With the main forum gone for the while being, this is a good example on how Twitter has become a tangible alternative to the media driven jihadists, for the Twitter accounts remain alive and very active with their over 26,000 followers, untouched by any disruptions of the forums. The YouTube link above is an “invitation to Muslims to visit the forum” and recommends and instructs the use of Tor to conceal one’s identity online.
@Al_nukhba
This account could be described as a jihadi media hub. The members, active on the forums for years, are highly committed and regularly produce transcriptions of jihadist media productions. This is naturally very helpful for any analyst but is also quite a service for the jihadi audience. Usually speeches of main leaders and ideologues as well as major video productions of as-Sahab, al-Malahem etc. are transcribed and can be conveniently downloaded as a PDF or Word document. For a first hand impression on the quantity and quality of this media department’s work, check out their contributions on the Shumukh al-Islam forum here.
On their main website data collections and videos can be downloaded and also searched for. It is a well built and maintained datawarehouse for extremist content that is first and foremost uploaded and disseminated via the classical forums. The Twitter account has about 6,000 followers, over 500 tweets, and is following no one.
This had been one of the pioneer jihadi Twitter accounts and advertised their social media passion as early as 2009. Perhaps the name nukhbat al-I’lami al-jihadi, “the Jihadi Media Elite”, stems from Abu Mus’ab al-Suri’s “Message to the British and European Peoples and Governments regarding the Explosions in London”, July 2005, where he outlined the Internet as the most important medium to propagate and spread the jihadists demands and frame of reference in general. He referred to “the jihadi elite” residing in Europe to partake in this venture.
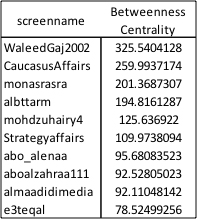
The ‘betweenness’ calculation highlights those users through which the shortest paths across the network most frequently pass. These users are often found near the centre of the network image. From the perspective of ‘betweenness’, in addition to some of the users mentioned above, also appear to have an important role bridging between different elements of the network.
To provide some additional insight in this, here is some basic information on
@Caucasusaffairs
The name of this account is program, everything related to the Caucasus, the Caucasus Emirate (analysis) with the focus on Chechnya is published here in mainly Arabic but also Russian. With over 44,000 followers while following over 400 and about 8,000 tweets this account is a valuable asset besides the main forums and their pertaining subsections. It mainly retweets the Arabic language media outlet “Echo of Caucasus” which is one of the main media hubs in Arabic for many years. You may note the four fingered black hand on the yellow background, a symbol to the Rabaa al-Adawiya protest camp whereby many pro-Mursi citizens were killed in Egypt recently. For more on this topic, check out the fantastic Closer blog here. The use of this icon in the Chechen context is yet another attempt by the media savvy jihadists to globalize their agenda and serves as proof for the repeated claim of the “war against Islam”. In the meantime this icon has been further ‘jihadised’ by adding the typical black banner, see here for example.
What does this tell us?
The density of the network has two results. First it creates mutually reinforcing clusters of information which can crowd out other perspectives and contribute to the development of a zeitgeist, or a new electronic propaganda frontier, as discussed in relation to activity of Jabhat al-Nusra.
Second, the density of the network tends to protect it against basic disruption strategies, for example the removal or suspension of individual accounts. As Paul Baran’s work On Distributed Communications has demonstrated only a small level of redundancy is required to build a communications systems to withstand heavy enemy attacks. Although this work was done in the context of the 1960s and was particularly focused on challenges faced in the 1970s, the insight provided by the study also relates to online activity and the need for more complex strategies to disrupt dense communication networks.